Brute-force Attack
This type of attack will try all possible character combination randomly. If you can't remember anything about the password, such as length, possible characters it contains, frequently used character set for your password. Then use this attack to help you get back lost password. However, this attack may cost relatively longer time than the other two types.
Brute-force with Mask Attack
You can use this attack if you still remember part of your password. For example, if you still remember your password is 4 characters and begins with "z", then you can define the mask as "z???". This reduces the work for the program, as it will seek for the last 3 characters of the password instead of 4 characters of the whole. To use this attack, a Password Mask must be defined.
Under "Brute-force", set the possible length for the password with "Min Length" and "Max Length". Define the possible password character settings with "Character Set":
- a-z: refers to the 26 small letters, abcdefghigklmnopqrstuvwxyz. If there is one or more lowercase letters in the password, check the box.
- 0-9: refers to the ten digits, 0123456789. If there is digit in the password, check the box.
- A-Z: refers to the 26 letters in upper case, ABCDEFGHIGKLMNOPQRSTUVWXYZ. If there is one or more uppercase letters in the password, check the box.
- -_!@#$%^&*: refers to special characters. If there is special character in the password, check the box.
- Custom Character Set: this is to let you enter the symbols that the ranges above do not include.
- Check the box of "Prefix", if you still remember the first character of the password and type it in the box immediately after.
- Check the box of "Suffix", if you still remember the last character of the password and type it in the box immediately after.
Dictionary Attack
This attack is highly recommended. If use properly, it is the fastest when compared with the above two attacks. This attack is intended to seek the possible password based on a dictionary. This dictionary can be the integrated one or the one you provide. The integrated dictionary is a text file listing common character combinations, such as a, ab, 123, 4, AB, etc. that people may frequently use for passwords. You can also create a dictionary by listing your character sets that you frequently use to let the program base on when seeking passwords. If so, the seeking scope is largely reduced and it is bound to save time for the process.
Under "Dictionary":
The program provides a default dictionary, which lists common password combinations in line. If want to use the default dictionary, then leave it as default. If you want to use your own dictionary, which is closer to the possible password, then create a text file, and list the possible characters and character sets included in the password in line, and then select the file as the dictionary for the program with "Select Dictionary File…"
For example, you are used to some password combinations, your birthday, like your name, your English name, etc. You can set them as a combination; you can create a dictionary as below:
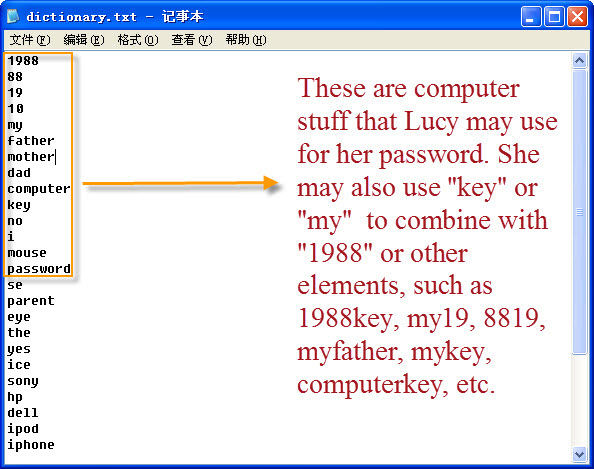
World's 1st Windows Password Recovery Software to Reset Windows Administrator & User Password.
Free Download Free Download